WInnForum Approved CBRS Root CA Operators
|
|
Insta: Root CA ID 0001
 
|
Request for Proposal to become An Approved CBRS Root CA Operator
The Wireless Innovation Forum’s Spectrum Sharing Committee is seeking candidates to be approved to operate a Root of Trust certificate for the CBRS Public Key Infrastructure as outlined in the following documents:
|
|
CommScope: Root CA ID 0004
|
|
The CBRS PKI is a three or four tier infrastructure with CBRS Root CAs at tier 1 that issue intermediate CA certificates (i.e., sub-CAs) at tier 2. The tier 2 sub-CAs issue compliant endentity Subscriber certificates or CBSD OEM CA certificates at tier 3. Tier 3 sub-CAs issue compliant end-entity CBSD Subscriber certificates (see Figure 1 ). There are up to 6 different CA chains anchored by a CBRS Root CA: SAS Provider, Domain Proxy, Professional Installer, PAL, CBSD Mfr, and CBSD OEM. The WInnForum will make the list of approved Root CAs available to Subscribers
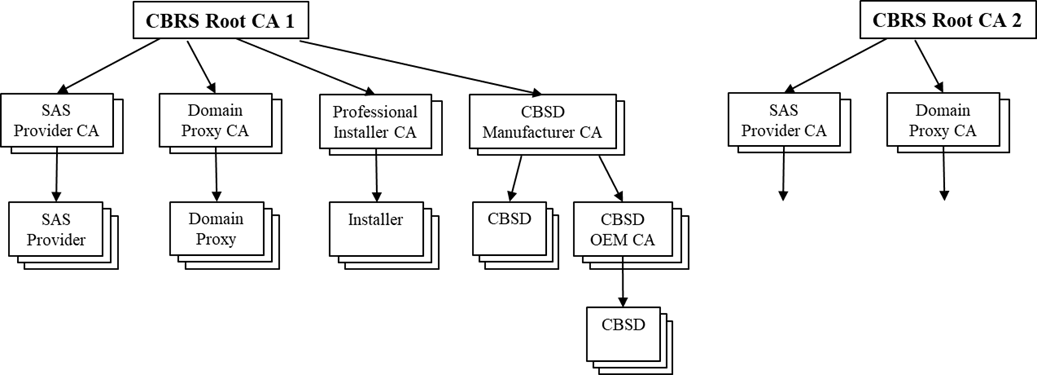
The CBRS Root CA is the apex of its Root CA Domain. The Root CA will issue the sub-CA certificates to approved CA service providers. The sub-CAs will issue certificates to authorized Subscribers, which will embed the certificates in compliant devices. It is a assumed that an Installer certificate will be installed in a device used by an authorized installer to manage/configure CBSDs.Subscribers should install all WInnForum authorized CBRS Root CA certificates in their device trust anchor stores to validate received certificates. The end-entity certificate, its private key, and all sub-CA certificates for a givenCA chain should also be installed on the device. During the TLS authentication messaging exchange the end-entity and all sub-CA chain certificates should be sent to the other end point.
To review the certificate policy in its entirely, you can download it here.
|
|